Tale of North Korea’s cyberterrorists: How they break into ‘unhackable’ crypto platforms and cash out
Experts say traditional tactics of manipulation still employed, but methods in cyberspace evolving
By Ji Da-gyumPublished : Dec. 12, 2022 - 18:18

Early this year, a senior engineer at Axie Infinity, a Vietnamese company that runs a popular blockchain-based play-to-earn game, was encouraged to apply for a lucrative job through LinkedIn.
But after the engineer opened a document file with a job offer letter, the network of the Ronin bridge, a platform created by Axie Infinity to transfer cryptocurrencies, was suddenly compromised. Spyware planted in the file enabled hackers to infiltrate the Ronin network and steal cryptocurrencies valued at $625 million in March.
While it may sound like fiction, that is just how the Lazarus Group penetrated Ronin bridge’s IT infrastructure and hacked validator private keys to steal cryptocurrencies. The US Federal Bureau of Investigation in April confirmed that the Lazarus Group is responsible for one of the biggest cryptocurrency heists of all time.
Lazarus Group is an army of North Korean state-sponsored hackers trained for life to pilfer illegal assets to fund the heavily sanctioned regime’s nuclear ambitions that keep leader Kim Jong-un in power. The $625 million the hackers stole from the Ronin bridge was equivalent to how much it cost Pyongyang to launch 31 ballistic missiles in the first half of this year, according to Seoul.
The Axie Infinity case is only the tip of the iceberg in regard to North Korea’s decadeslong history of financial crime. They no longer steal from banks, but now break into cyberspace by manipulating people and stealing money from online financial systems with sophisticated technological know-how.
Millie Kim, a researcher with the North Korea Cyber Working Group, an initiative of the Korea Project at Harvard University’s Belfer Center for Science and International Affairs, said, “North Korean state-sponsored hackers are adept at tracking developments in the crypto space, especially when it comes to identifying vulnerabilities in the latest blockchain technologies.”
“Part of this has to do with open access to online information, and another part is the strategic placement of overseas workers in IT and cryptocurrency firms to transfer specialized knowledge to hackers,” Kim said.
“Talent cultivation and training of cyber agents at state institutions and other foreign countries provide another crucial means through which North Korea can experience and obtain information about rapidly evolving blockchain technology.”
Park said the “BlueNoroff group contacted the victim through social media to get trust” and then “deliver sophisticated malware with multistage infection stages.” Next, North Korean hackers “collect the victim’s general information and monitor how the victim handles cryptocurrency for a sufficient period.”
In general, North Korean cybercriminals “gather organizational information, identify vulnerable individuals and weakness in infrastructure and analyze the behavior of their targets” before deploying advanced social engineering tactics, according to a Chainalysis report carried in the midterm report of the Panel of Experts issued this September.
In addition, the Lazarus Group-affiliated cyberthreat actors have mastered and refined techniques of creating fake personas, establishing fictitious businesses and carefully curating digital identities to “communicate with and gain the trust of their targets.”
North Korean threat actors have created “fake-yet-legitimate-looking accounts” on social media platforms such as LinkedIn and Twitter, regularly uploaded content and engaged in personal and curated conversions with their targets. Then, North Korean hackers launch a spear-phishing attack through various channels, including sending emails with malware-ridden attachments or malicious links, an invitation to collaborate through SharePoint and sharing Google Docs links.
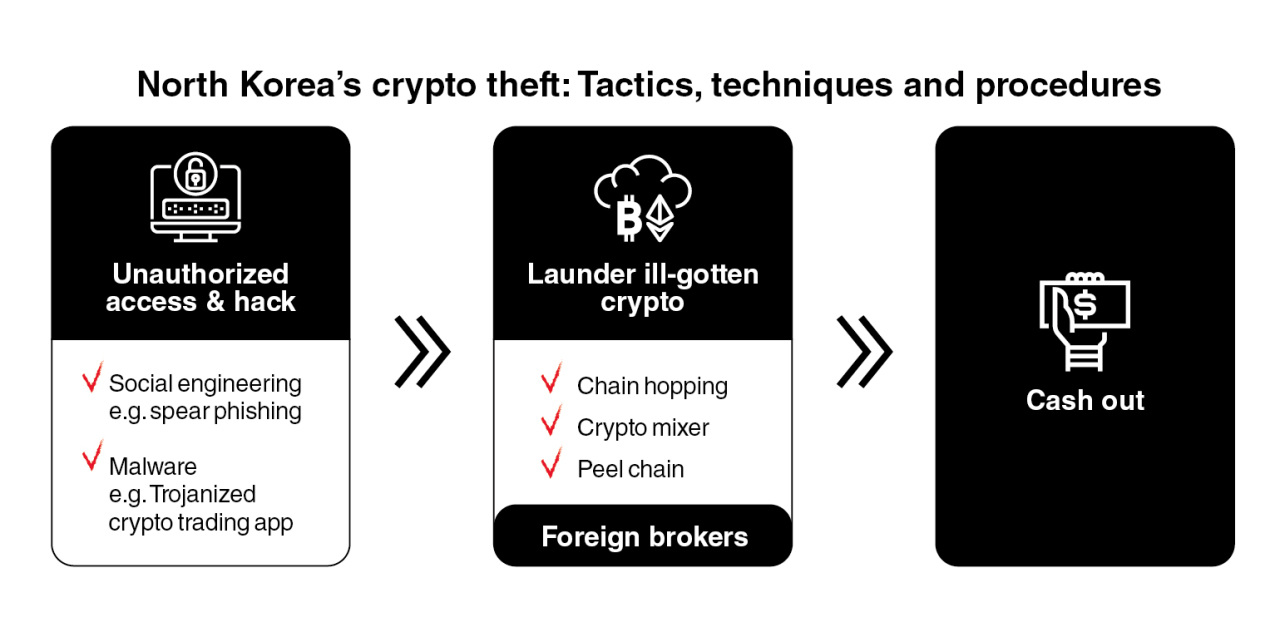
North Korea’s fake persona Kim Hyon-woo was used to attack Sony Pictures Entertainment, conduct cyberheists against financial institutions including Bangladesh Bank and target US defense contractors, according to the US criminal complaint unveiled in 2018.
North Korean state-sponsored hackers have mainly used two off-chain tactics: social engineering and malware. Hacking groups have generally used traditional espionage tactics such as advanced social engineering attacks to break into cryptocurrency systems by deceiving and luring victims into inadvertently providing access to their network and classified information or downloading malware-ridden files.
Social engineering is a psychological manipulation technique that exploits human nature and tricks people into giving up confidential information and bypassing security procedures.
One example could be a spear-phishing campaign that scams a specific person or group by sharing information known to be of interest to the target through legitimate-looking emails or electronic communications.
In addition, North Korean cyber actors attacked individuals and organizations including cryptocurrency exchanges and financial services for cryptocurrency theft by disseminating malware-ridden cryptocurrency trading applications, according to the US Joint Cyber Security Advisory issued in 2021.
North Korean cybercriminals “use phishing, social networking, and social engineering techniques to lure users into downloading the malware” dubbed by the US government as “AppleJeus.”
In general, legitimate-looking companies advertise and distribute a modified, trojanized version of a cryptocurrency trading application on their website.
In 2020, North Korean cyber actors targeted institutions in the fields of energy, finance, government, industry, technology and telecommunications for cryptocurrency theft with the AppleJeus malware in over 30 countries.
“Going for cryptocurrencies plays to the strengths of North Korea’s cyber operators, as it leverages skills from across ‘traditional’ intrusion sets as well as those individuals that are doing IT/freelancer work online,” said Joe Dobson, a senior principal analyst at Mandiant, based in Virginia.
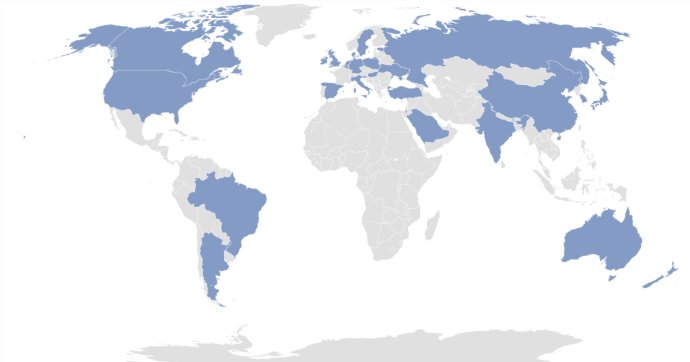
But running off with cryptocurrency is only the start. North Korea has engaged in multistage and sophisticated laundering processes to cash out the ill-gotten cryptocurrencies.
“The Kim regime has become proficient at mixing and laundering funds to try to obfuscate the origin of its stolen funds,” said Annie Fixler, deputy director of the Center on Cyber and Technology Innovation at the Foundation for Defense of Democracies in Washington.
North Korean state-sponsored cyberthreat actors have used various tactics to conceal or obfuscate the source of ill-gotten cryptocurrencies and illicit transactions without providing identification or "Know Your Customer" information.
“To launder the funds, they use obfuscation techniques such as mixing, using services like Tornado Cash to create a disconnect between the cryptocurrency they deposit and withdraw, and chain hopping, which is the process of swapping between several different kinds of cryptocurrency in a single transaction,” said Erin Plante, vice president of investigations at New York-headquartered Chainalysis.
In general, North Korea launders stolen cryptocurrencies largely by chain hopping tools, mixers and peel chain techniques.
Chain hopping is a tactic of moving between different types of cryptocurrencies often in rapid succession. A peel chain is a technique of laundering a large amount of cryptocurrency through a long series of small transactions.
A cryptocurrency mixer is a software tool that pools and scrambles cryptocurrencies from thousands of addresses to obscure and conceal the flow of transactions.
“North Korea tends to rely on mixers and blockchain hoping. However, they will always use the path of least resistance,” said Allison Owen, a research analyst at the London-based Royal United Services Institute. “It is critical to continue to look at the horizon to restrict any emerging areas that they can exploit.”
Cybersecurity experts and blockchain analysts also underscored that more attention should be paid to North Korea’s collaboration with foreign countries and nationals in each stage of cryptocurrency robbery.
North Korea also has a history of conspiring with foreign nationals, including Canadian American and Nigerian partners to launder funds from North Korean-perpetrated cyber-enabled heists.
Nick Carlsen, a blockchain analyst at TRM Labs and a former FBI analyst, said such collaboration with foreign nationals is more important in the phases of laundering and cashing out stolen funds.
For instance, over-the-counter brokers “play a major role in each stage” of laundering stolen funds through layering schemes to move and transfer ill-gotten cryptocurrency into different wallets and currencies, according to a report issued in May by the Belfer Center for Science and International Affairs.
The OTC system allows parties to buy and sell securities outside of formal exchanges and through decentralized dealer networks.
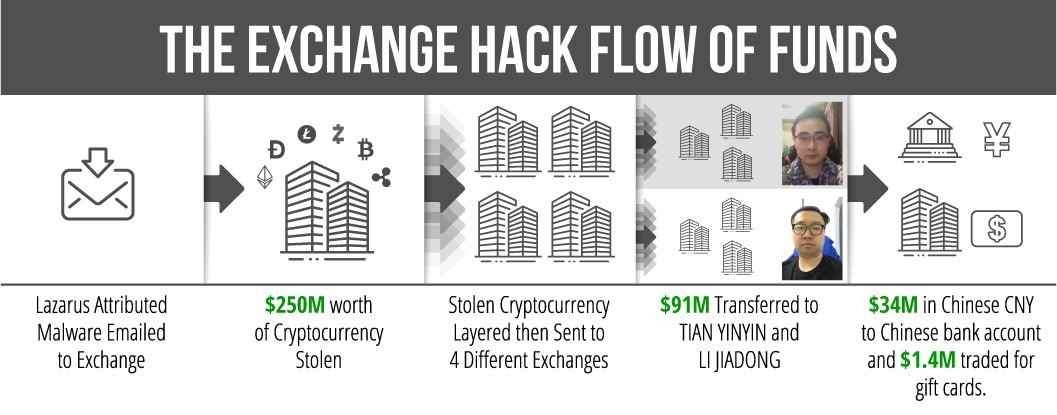
Two Chinese nationals were charged with laundering over $100 million in cryptocurrency — stolen by Lazarus Group from cryptocurrency exchanges — between 2017 and 2019, the US Treasury Department and Justice Department said in 2020. One Chinese national moved more than $34 million of ill-gotten cryptocurrency through a Chinese bank account and transferred around $1.4 million of bitcoin into Apple iTunes gift cards.
Robert Potter, co-founder and co-CEO of Australian-US cybersecurity company Internet 2.0, also pointed out that “Russia and China have been content to turn a blind eye” to North Korea’s cryptocurrency theft.
“North Korean-linked hackers have used services located in countries all over the world, including China and Russia, to attempt to cash out their ill-gotten gains,” Plante from Chainalysis said.



















![[Today’s K-pop] Treasure to publish magazine for debut anniversary](http://res.heraldm.com/phpwas/restmb_idxmake.php?idx=642&simg=/content/image/2024/07/26/20240726050551_0.jpg&u=)