NK’s Lazarus Group hacked 61 S. Korean media, organizations: police
Hacking group exploited vulnerabilities in security software for online banking installed on over 10 million computers
By Ji Da-gyumPublished : April 18, 2023 - 16:49

North Korea’s state-sponsored hacking group conducted a series of cyberattacks targeting South Korean public and private organizations by leveraging websites of South Korean media outlets to distribute malware, the South Korean police said Tuesday. But South Korea has foiled the Lazarus Group’s potential attempts to launch hacking attacks on a massive scale.
The Lazarus Group hacked into 61 organizations, including eight South Korean media outlets, as well as biomedical and defense companies, by exploiting vulnerabilities in cybersecurity software for financial services and online banking which is installed on over 10 million computers in South Korea, the Korean National Police Agency said.
A total of 207 computers were compromised since last June, according to the outcome of a monthslong joint investigation by South Korean government agencies that began in November last year.
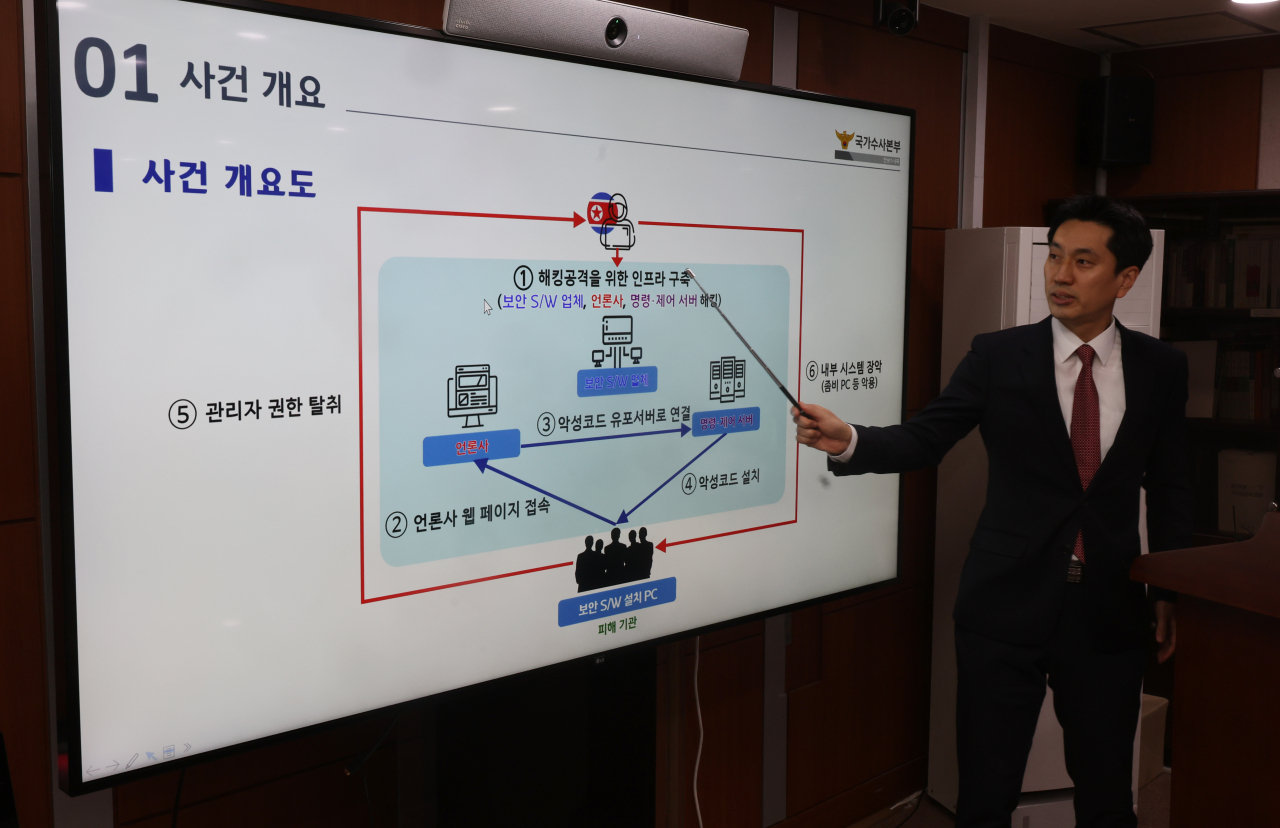
The specific hacking scheme used by the Lazarus Group was unraveled by the South Korean police.
The elite North Korean hacking group launched “watering-hole” attacks from the websites of South Korean media. The media outlets were not named.
A watering hole attack is a targeted attack in which cybercriminals seek to compromise a specific group of end users either by infecting websites they typically visit or luring them to a malicious site. The goal is to infect an end user’s computer with malware and gain access to an organization’s network.
In this case, the websites of South Korean media companies are compromised to enable the distribution of malware.
When a victim whose computer has a defective version of the online banking security system visited a virus-infected website of a relevant media outlet, the malware would be automatically distributed and downloaded onto the victim’s computer. Through the scheme, the Lazarus Group hacked into the networks of scores of South Korean organizations.
The Lazarus Group had “meticulously prepared for cyberattacks” for around one year since hacking into the Initech company, which is an affiliate of KT and BC Card, in April 2021 to identify vulnerabilities of its Inisafe CrossWeb EX V3 program, according to the police.
The police also warned that the recent series of cyberattacks could be developed into massive hacks that cause “widespread damage,” citing two main reasons.
The Lazarus Group notably “exploited weaknesses of the software that are essential for using online financial services such as internet banking and used media websites that are accessed by the majority of the people as a means of distributing malicious codes,” the police explained.
According to the police, Lazarus had initially planned to hack computers and turn them into so-called “zombies” which are under the control of a hacker to launch cyberattacks on a massive scale targeting South Korean institutions, but such attempts were foiled.
“We cannot rule out the possibilities of (the Lazarus Group) preparing for a large-scale cyberattack by exploiting vulnerabilities in security software for financial services installed on over 10 million computers in the country,” the police said.
“However, we’ve preemptively detected and blocked such attempts in coordination with relevant agencies.”
The South Korean police called for people and organizations to update the software to the latest version to patch the vulnerabilities and prevent further damage as “North Korea’s hacking techniques are becoming increasingly sophisticated.” Around 80 percent of computers have updated defective software to the recent version as of Friday.
The National Police Agency also unveiled its plans to launch an international investigation into cyberattacks that were conducted overseas and also targeted foreign institutions, as well as continue its own investigation into additional cases of damage and similar hacking attempts in South Korea.
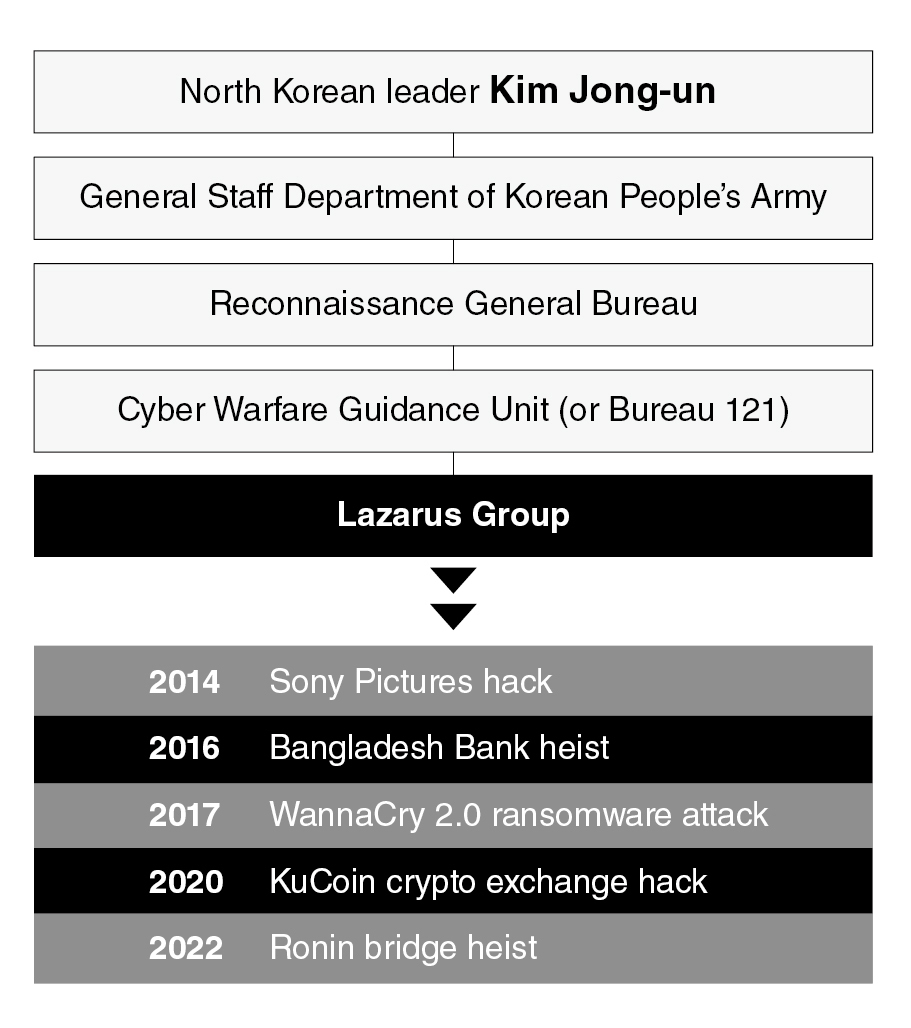
Since 2009, the Lazarus Group has been behind nefarious cyber activities. The list includes the destructive WannaCry 2.0 ransomware attack in 2017, which affected 300,000 computers in over 150 countries and caused billions of dollars of damage; the 2016 Bangladesh bank heist; and the 2014 cyberattack on Sony Pictures Entertainment.
The hacking group also has been also accused of committing high-profile cryptocurrency thefts, including the $625 million Ronin bridge heist in March 2022 and the $275 million hack from KuCoin in 2020.
The Lazarus Group, already sanctioned by the US and South Korea, is being controlled by North Korea’s principal intelligence agency, the Reconnaissance General Bureau, which oversees foreign business including weapon sales. The RGB, under the umbrella of the General Staff Department of the Korean People’s Army, is sanctioned by the United Nations and the US.










![[Hello India] Hyundai Motor vows to boost 'clean mobility' in India](http://res.heraldm.com/phpwas/restmb_idxmake.php?idx=644&simg=/content/image/2024/04/25/20240425050672_0.jpg&u=)









